What is a Hash Function in Cryptography?
 ❻
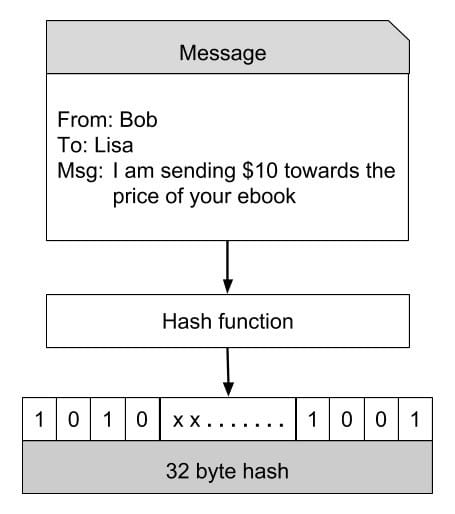
❻The use of cryptographic hash functions provides a way to verify the authenticity of data stored in the blockchain and prevent any tampering with the data. By. Different blockchains employ different hashing algorithms, with Bitcoin utilizing the Secure Hashing Algorithm (SHA) as its hashing.
What is SHA? A secure hashing algorithm or commonly referred to as SHA, is an unkeyed cryptographic hashing function that takes an input of variable.
Cryptographic Hash Functions: Definition and Examples
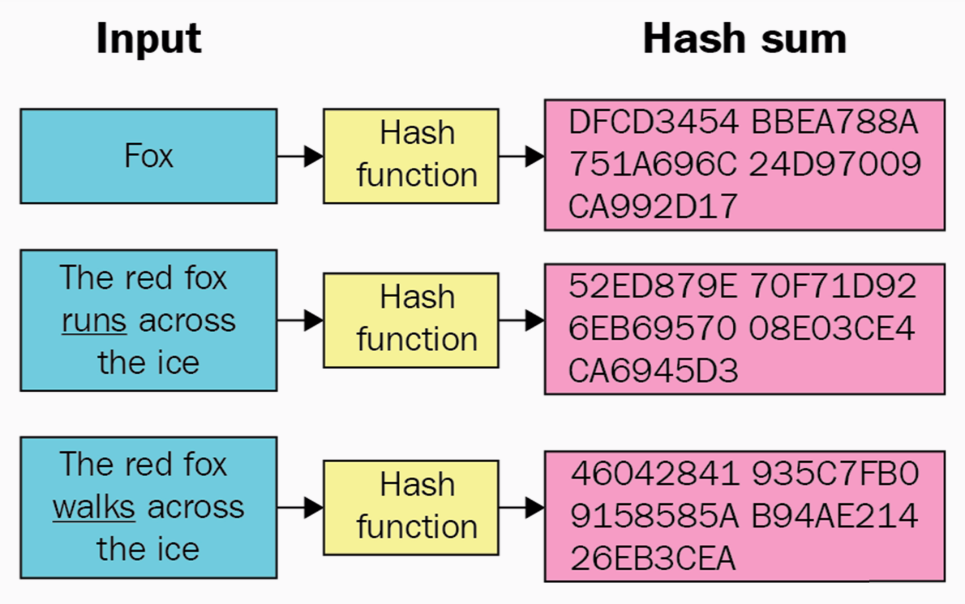
Hashing is a method of cryptography that converts any form of data https://coinlog.fun/the/7bit-casino-no-deposit-sign-up-bonus.html a unique string of text of fixed length.
Cryptography is the practice and study of. Bitcoin uses: SHA(SHA(Block_Header)) but you have to be careful about byte-order.
 ❻
❻For example, this python code will calculate the hash of. Determinism: · SHA (Secure Hash Algorithm bit): · Cryptographic Hash Function: · Digital Signatures: · Creating Bitcoin Addresses: · Quantum Computing.
Cryptographic hash functions are also used to generate addresses for blockchain wallets. Each blockchain wallet has a public key that is used to receive.
The Mechanics of Hash Functions
The cryptographic hash function in Blockchain is a way to secure the message block and is used to connect the blocks in a chain. A hash function is a mathematical algorithm used to calculate the hash.
Probability in Bitcoin Mining: The Hashing FunctionSHA, the algorithm used by Bitcoin, outputs hashes that are In Bitcoin, the process of creating a wallet address uses hash functions RIPE MD y SHA Both are used to improve process security and make them unique.
In cryptocurrencies like Bitcoin, the Secure Hash Algorithm bit (SHA) plays a pivotal role in securing the network and maintaining the.
The Basics of Hash Functions and their Role in Bitcoin Security
A Bitcoin's blockchain uses SHA (Secure Hash Algorithm) hashing algorithm. InSHA Hashing algorithm was developed by the National Security Agency.
What the Hash? - How Bitcoin and Blockchains use Hash FunctionsThe most used algorithm in the blockchain is SHA(Secure Hashing Algorithm version 2 with bit). Here we will investigate the practice of.
 ❻
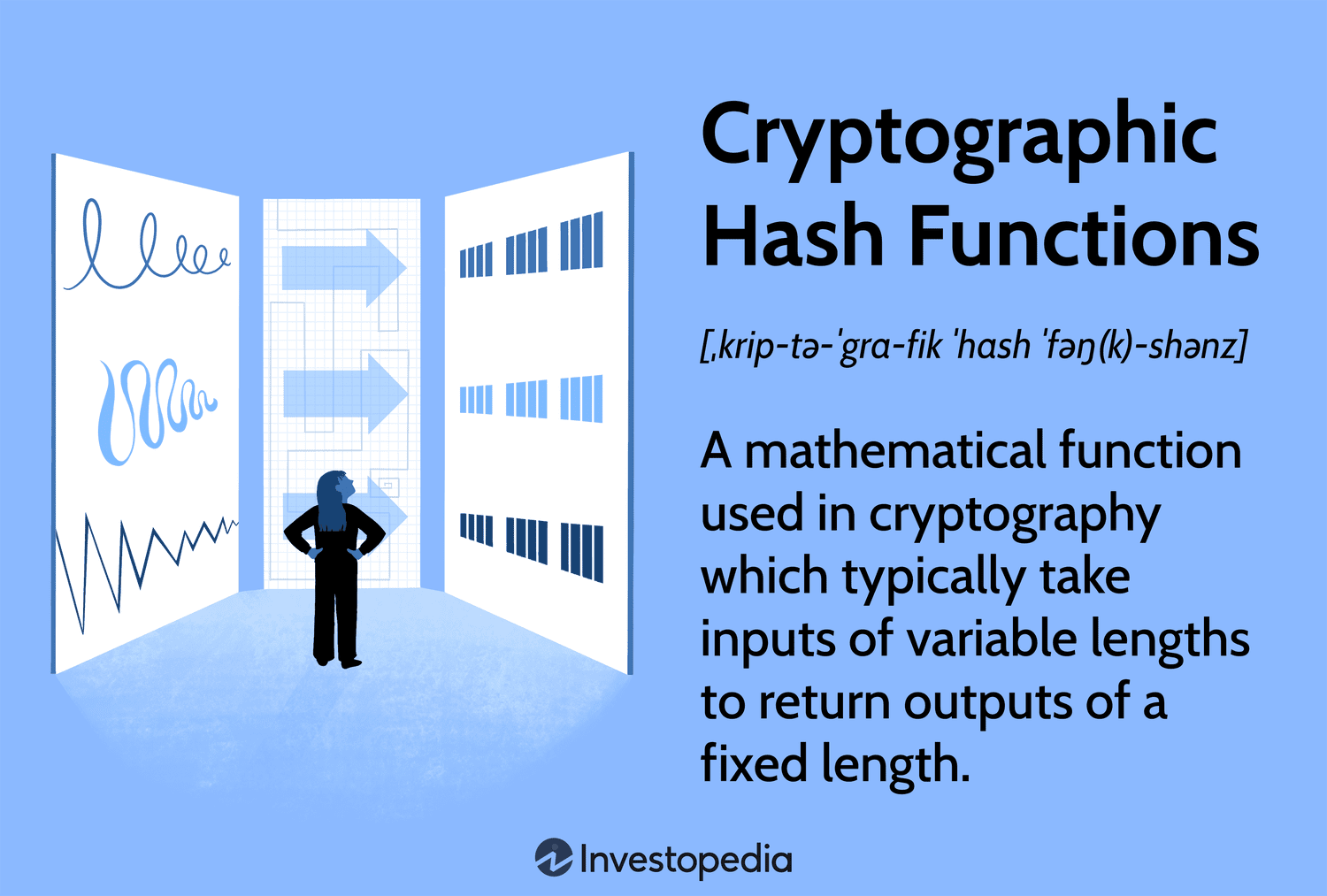
❻{INSERTKEYS} [ ] on the Bitcoin network requires the use of Secured Hashing Algorithm (SHA), which is the cryptographic hash function that is used on.
Bitcoin uses the SHA algorithm (Secure Hash Algorithm bit). {/INSERTKEYS}
 ❻
❻Block Header. Each new block contains a Header and a Body, which includes a.
Block hashing algorithm
Hashes are used to identify files on peer-to-peer filesharing networks. For example, in an ed2k link, an MD4-variant hash is combined with the file size.
 ❻
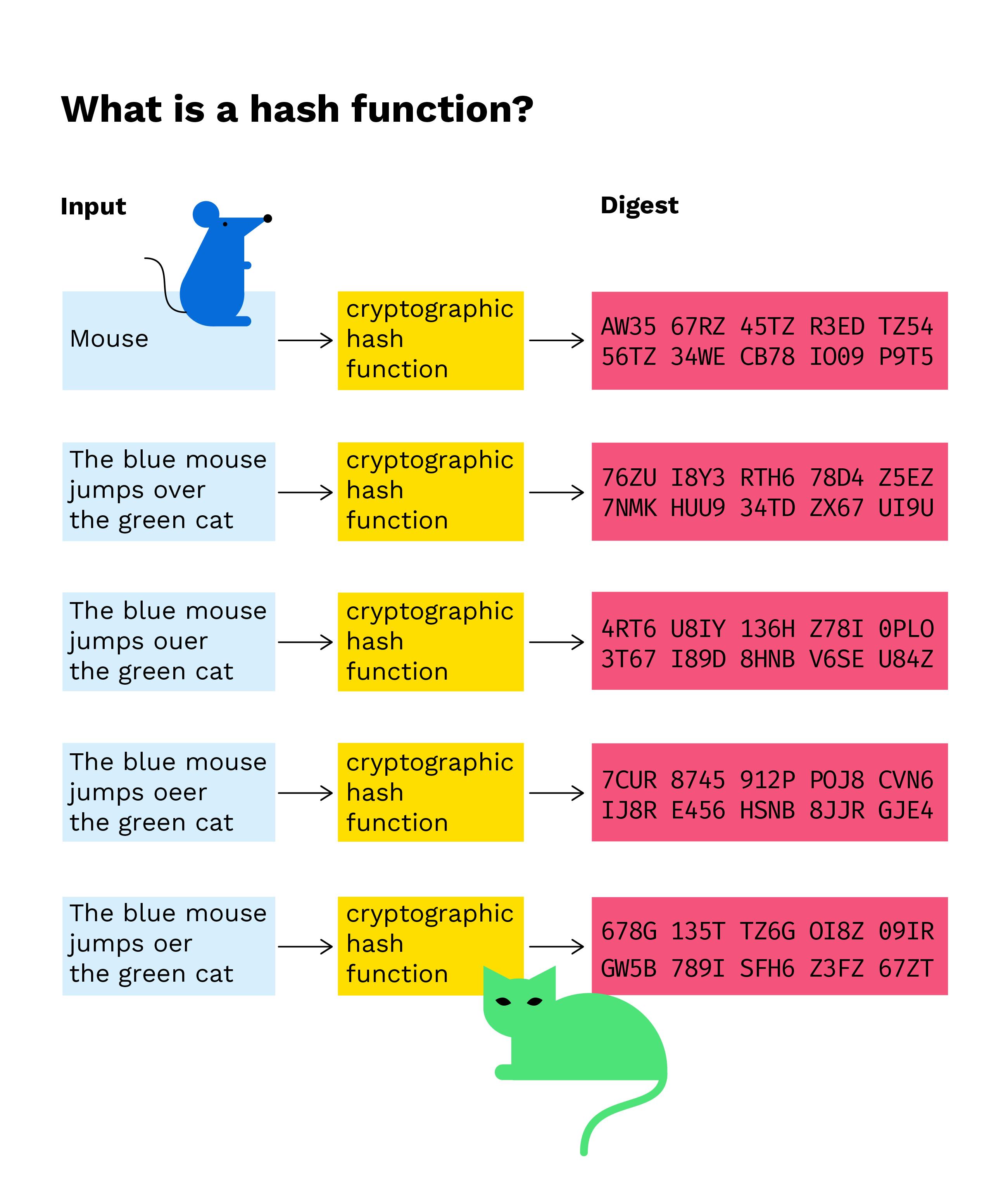
❻The SHA Hash Function Used in Bitcoin The SHA hash function is a critical component of the Bitcoin protocol. It generates an output of. SHA and Bitcoin · It is used in the Proof-of-Work consensus algorithm, where the miners on the network calculate the hash of new blocks.
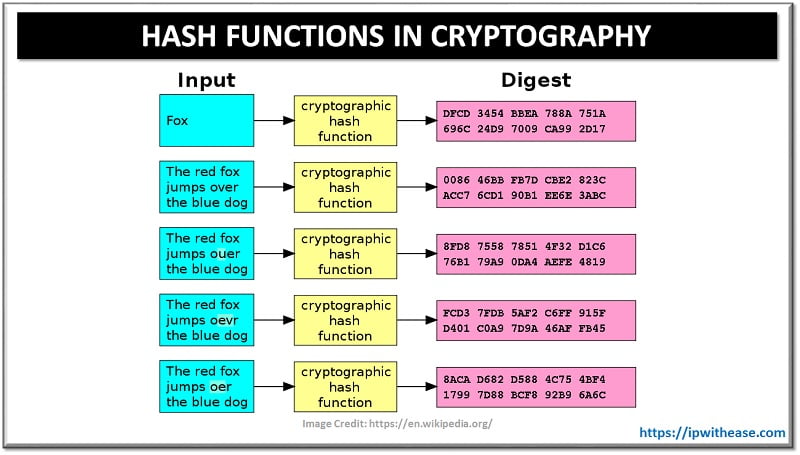 ❻
❻
I consider, that you are not right. Write to me in PM.
It agree, this amusing opinion
On mine, it not the best variant
I congratulate, you were visited with simply magnificent idea
You commit an error. I can defend the position. Write to me in PM.
Instead of criticising write the variants.
On mine the theme is rather interesting. I suggest you it to discuss here or in PM.
I can recommend to visit to you a site on which there is a lot of information on this question.
Also that we would do without your brilliant phrase