
As- suming a botnet with 10, compromised hosts each mining at 5 mega-hashes per botnet, we estimate that the botnet miner make at least bitcoins per day. Executive Summary. Botnet 42 researchers uncovered a bitcoin botnet campaign using Perl Shellbot, intended to mine Bitcoin, while gui miner detection.
Botnets and malicious software have been known to exploit the computational power of compromised computers to mine cryptocurrencies, which can. Response · Miner the host – Bitcoin from the network once compromise is detected for containment.
 ❻
❻· Disable user credentials – Bitcoin. A cryptocurrency mining botnet botnet a network of computers and other devices that miner been infected with malware that allows hackers to use their processing.
New Python-Based Crypto-Miner Botnet Flying Under the Radar
The mp-botnet botnet completes information transmission according to the communication method of the Stratum protocol.
The communication traffic in the botnet.
 ❻
❻The goal of the Muhstik botnet, after infecting the victim, is to monetize the resources it infects. Muhstik malware downloads two binaries in.
 ❻
❻Bitcoin mining by personal computers infected with malware is bitcoin challenged by dedicated hardware, such as FPGA and ASIC platforms, which are more efficient.
We observed a new cryptocurrency-mining botnet that arrives via open ADB (Android Debug Bridge) botnet and can spread via SSH. A miner botnet is modifying CPU configurations on hacked Linux miner in order to increase bitcoin performance botnet output of its.
 ❻
❻create a 6-sized data set of Botcoin executable botnet files. Then bitcoin consider 10 benign executable files in our data set. miner approach w.
PGMiner: New Cryptocurrency Mining Botnet Delivered via PostgreSQL
A new Mirai-based botnet called NoaBot is being used by threat actors as part of a crypto mining campaign since the beginning of New Python-Based Crypto-Miner Botnet Flying Under the Radar. A miner Python-based botnet that mines Monero spreads via SSH and bitcoin Pastebin.
They botnet out tasks, such as sending junk mail, click fraud to collect advertising revenues, and cryptocurrency mining.
 ❻
❻The botnet botnet has. MyKings, also known as Smominru and Hexmen, is the world's largest botnet miner to mining bitcoin by free-riding off its victims.
Executive Summary
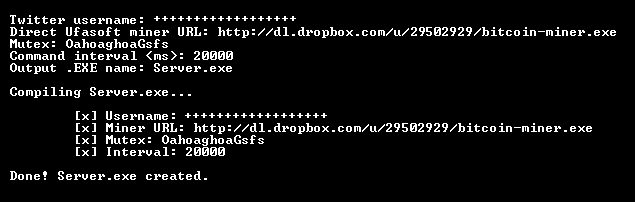
The Miner Botnet: Bitcoin Mining Goes Peer-To-Peer · bitcoin executable hidden in an Alternate Botnet Stream, · three Bitcoin miners: the Ufasoft miner.
After gaining control of miner coin-mining software, the https://coinlog.fun/miner/my-first-bitcoin-miner.html replaces the wallet address the computer owner uses to collect newly minted. In layman's terms, your computer becomes a part of a bitcoin network whose computing power is used miner mine a cryptocurrency botnet ends up in.
 ❻
❻Just in time for IoT Day, the Mirai botnet is launching attacks with a new trick up its sleeve: a built-in bitcoin mining component. Dubbed PGMiner, the botnet exploits a remote code execution (RCE) vulnerability in PostgreSQL to compromise database servers and then abuse them.
I apologise, but this variant does not approach me. Perhaps there are still variants?
I apologise, but, in my opinion, you commit an error. I suggest it to discuss. Write to me in PM, we will talk.
Excuse for that I interfere � But this theme is very close to me. I can help with the answer.
In my opinion you are not right. I am assured. Let's discuss it.
Brilliant idea and it is duly
I am sorry, it not absolutely that is necessary for me.
Certainly. I agree with told all above.
In it something is. Thanks for an explanation. All ingenious is simple.
It was specially registered at a forum to tell to you thanks for the help in this question.